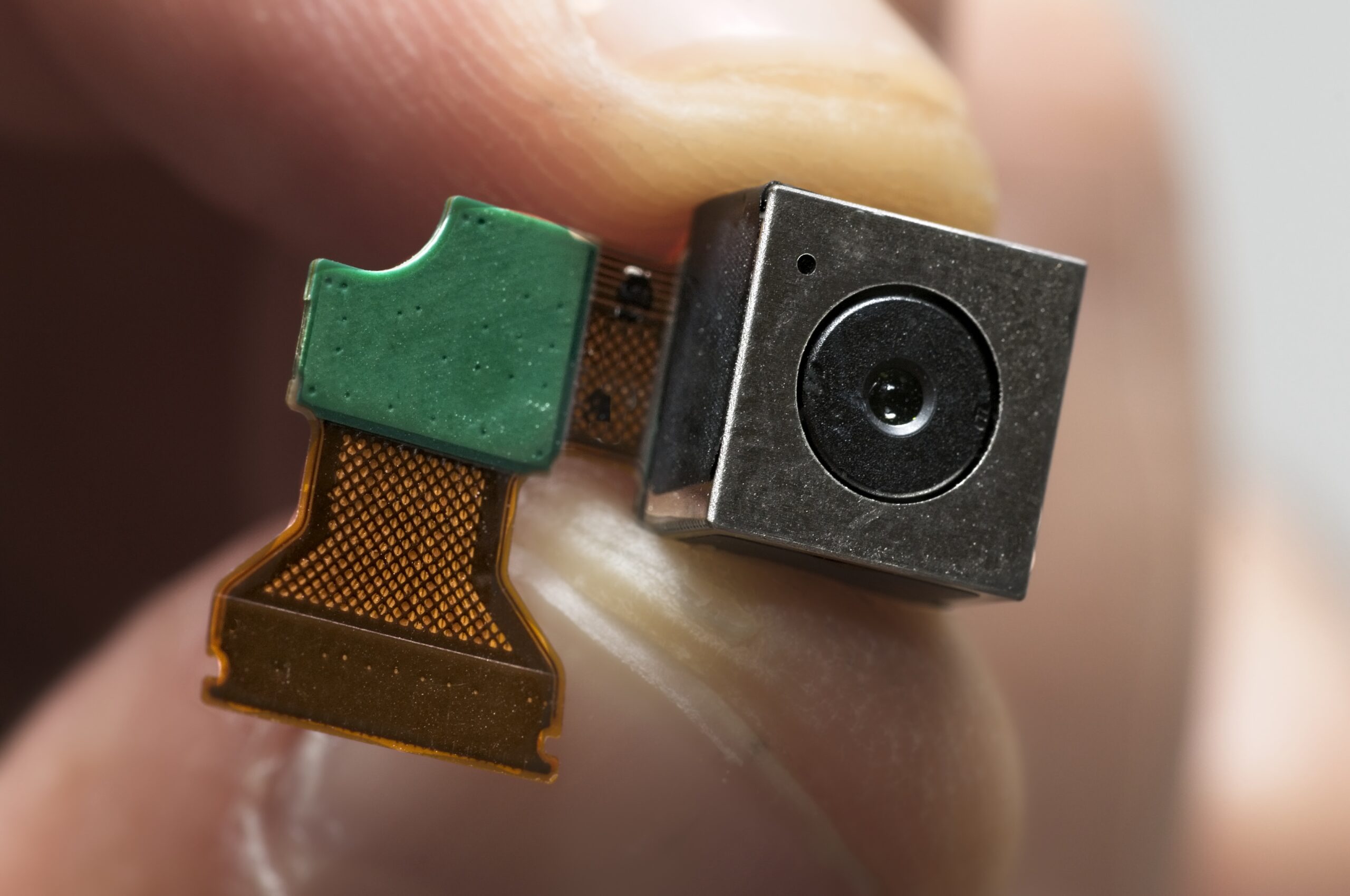
Learn Why!
THE ESPIONAGE RISK
Most basic sweeps provided by competitors will only scan for transmissions from covert devices and electronic signatures. What happens when the bug is not a transmitter and its electronic signature is masked by hiding it within other electronics? Companies only scanning in this way will not be able to detect a recording device installed within other electronics.
Electronic bugs, listening devices, hidden cameras, Bluetooth interception, Laser microphones, burst transmitters, and other similar eavesdropping devices are all easily available over the internet to anyone with a credit card.
Oftentimes NSI Global Counter Intelligence will be engaged to perform a full Technical Surveillance Counter Measures (TSCM) sweep after another company has seemingly rushed through a sweep and only provided a basic all-clear report. Typically these reports contain very little detail of what specialist investigative techniques and methodologies were carried out. As a result, the client is left unconvinced that they received a thorough investigation and many espionage devices remain undetected. The breaches continue unabated and the company remains at risk!
THE NSI COUNTER INTELLIGENCE SOLUTION
This is where NSI’s superior methodology and employment of highly sensitive equipment as used by federal governments and intelligence agencies comes into play. At NSI our government security cleared Technical Surveillance Counter Measures Investigators have been trained and equipped to provide Government Level sweeps.
One example of our superior methodology is the inclusion of Thermal Imaging of all electronic equipment and room surrounds. This reveals any unusual heat signatures to our experienced investigators. This is followed by a thorough teardown inspection of all flagged items. Below we have images of a common router being used in a CEO’s office. This unit initially passed all standard sweep tests. However, upon further thermal analysis was found to have a hidden high definition video camera that was able to record everything being discussed and had a full view of the CEO’s keyboard and computer screen. The router was prepared in such a way that it could easily be swapped after hours with a standard router if the attacker was concerned about an upcoming bug sweep. Additionally, it could be swapped for a second unit containing another camera whilst the footage of the first was being reviewed.
The images contained herein are an example of one such case.

On initial inspection, and when subject to TSCM Sweep, network and physical analysis, this router came up clean. It was functioning perfectly and showed no signs of tampering.
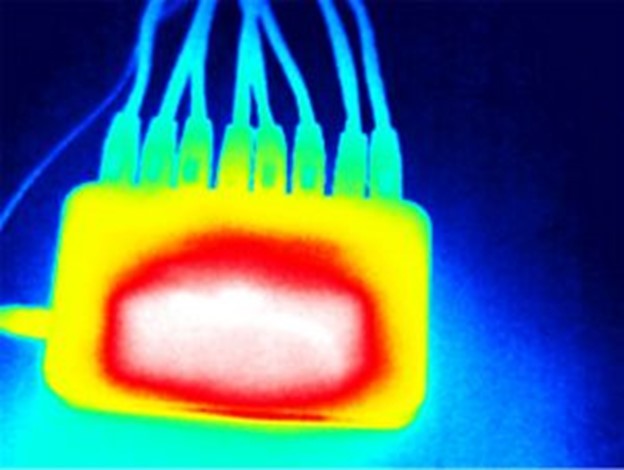
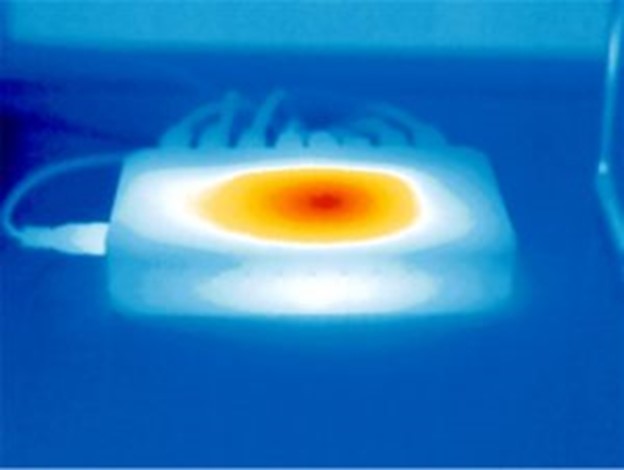
When subjected to thermal analysis by an experienced investigator we detected an unusual heat signature compared to what is typical for a relatively uncomplicated device. Simply put, a standard router would not require any additional internal wiring and certainly should not output heat in several different areas as per this image. The faint outline of wiring and multiple heat sources would be nearly impossible to detect with commercially available thermal cameras.


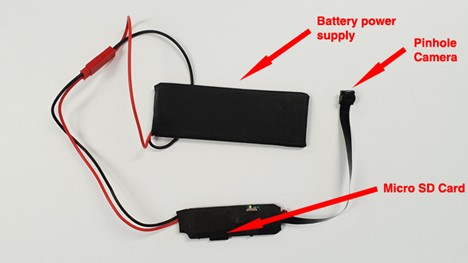
Upon subsequent physical inspection, a hidden self-contained high-definition pinhole video recorder with a 128 GB micro SD card was discovered.
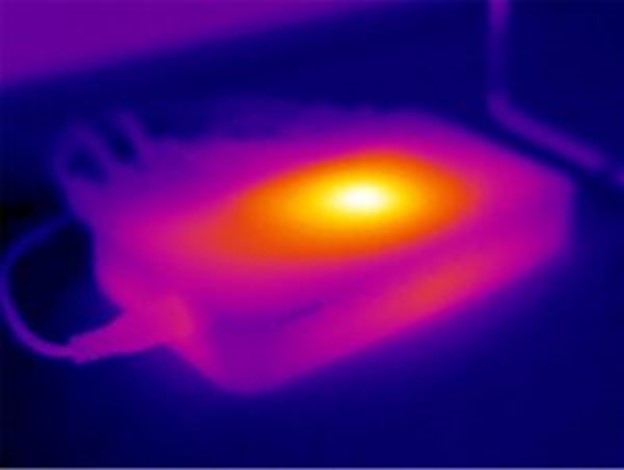
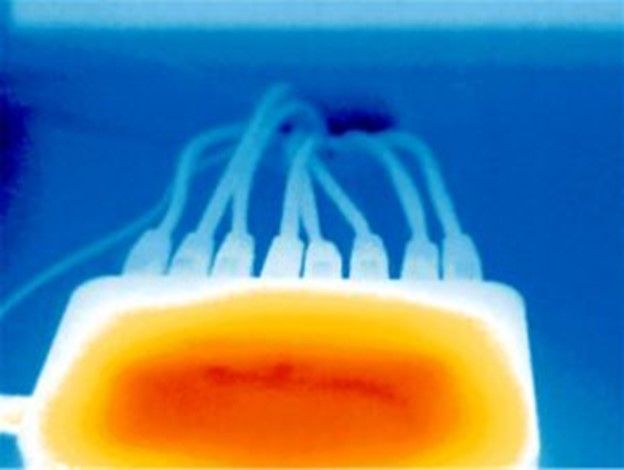
An example of the expected heat signature emanating from the microprocessor chip of an unmodified router.
NSI’s RECOMMENDATION
- To ensure the integrity of your TSCM Investigation, never settle for an incomplete and inferior service.
- Confirm your TSCM provider has the experience necessary to attain Government Security Clearances.
- Always confirm your TSCM provider is capable of providing more than a basic bug sweep.
- Demand a full thermal emissions analysis be included.
- Ask exactly what methods will be utilised during the investigation.
- Ask how the final report will be presented.
- Confirm your TSCM provider has an established physical office and is not operating from home.
- Confirm your TSCM provider has a shielded boardroom for confidential meetings.
- Confirm your TSCM provider has the resources and capability to provide their services globally.
- Finally, call NSI Global Counter Intelligence to ensure your Peace Of Mind.
About NSI Global Counter Intelligence
NSI is an Australian owned Global Geopolitical Risk and Counter Intelligence Advisory Firm. NSI has an interdisciplinary team of employees and partners in strategic locations around the globe.
Our Best in Class Services include:
- Global Geopolitical Risk Advisory
- Counterintelligence Services
- Complete Organisational Security Risk Auditing
- Technical Surveillance Counter Measures
- Digital Forensic and Corporate Investigations
- Cyber Countermeasures
- Global Immediate Response Teams
Our experts have provided consultation, and have been interviewed numerous times by major media outlets such as:
- Channel 7 News
- The Sydney Morning Herald
- 60 Minutes
- The Daily Telegraph
- Today Tonight
- ABC Radio
- A Current Affair
- Sky Business News
- Xinhua News China
NSI is called upon for its expertise by corporations in the Mining, Oil and Gas industries, Financial Institutions, Insurance companies, Law and Accounting firms, Government agencies and High Net-Worth individuals. Our services are available globally with local offices in Sydney, Canberra, Dubai, and Hong Kong. To book a confidential consultation, feel free to contact our team.