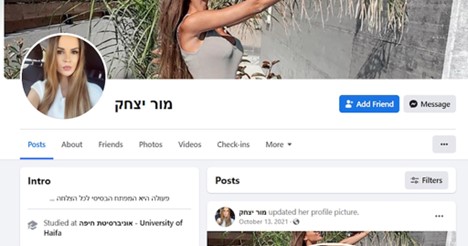
A Hamas-linked attack group called APT-C-23, is said to be involved in a sophisticated catfishing campaign targeting high-ranking Israeli officials. Beyond elaborate Facebook-focused social engineering, the group has introduced new malware including a fake messaging app (known as VolatileVenom), a downloader (known as Barbie Downloader), and a backdoor (BarbWire Backdoor).
The campaign individually targets high-profile officials working in defense, law enforcement, emergency services, and other government-related organizations. The purpose appears to be espionage. The campaign was discovered and analysed by Cybereason’s Nocturnus researcher team.
APT-C-23 and Molerats are thought to be the two primary sub-groups of the Hamas cyberwarfare division. Molerats has been active since at least 2011 and it focuses on the Middle East. It’s also tracked as Gaza Hackers Team, Gaza Cybergang, DustySky, Extreme Jackal, Moonlight, and TA402 — some researchers believe there are multiple groups operating under the same umbrella. Hamas is classified as a terrorist group in most of North America and Europe. ‘Catfishing’ is the creation of a fake online identity, using part or all of genuine identity, with the usual intent to damage reputations. In this case, the purpose is to create a very realistic identity that can be used to ensnare victims. The current campaign has been dubbed, Operation Bearded Barbie.
The attacks start from a fake (catfished) Facebook network of attractive females, report the researchers. The accounts are established and well-maintained, with the attackers joining relevant groups, posting in Hebrew to those groups, and friending friends of the targets, in order to give the profiles an even more authentic appearance. The group uses the accounts to “like” various Facebook groups and pages that are well known to Israelis, such as Israeli news pages, Israeli politicians’ accounts, and corporate pages. The purpose is to connect with the officials and slowly draw them into a virtual sexual relationship.
Once this connection is made and Facebook chats established, the catfish attacker suggests migrating to WhatsApp. This immediately gives the attacker the target’s phone number. As the conversations become more personal and sexual, the attacker suggests they should use a ‘safer’ and more ‘discrete’ means of communication. A specific Android app is recommended.
The Android app is really the VolatileVenom malware. On pre-Android 10 devices, the icon is hidden; on post-Android 10 the malware uses the Google Play installer icon. But when the victim attempts to sign in to the application, an error message is shown announcing the app will be uninstalled. VolatileVenom remains running in the background with a wide range of espionage capabilities.
Separately, the attacker also offers to send the victim a private video. This is delivered as a .rar file that comprises the video and the Barbie Downloader. “The video,” say the researchers, “is meant to distract the victim from the infection process that is happening in the background.” The infection process includes performing anti-analysis checks and gathering system information.
If the downloader assesses the host to be suitable, it connects to an embedded C2 server (otherwise it just terminates). The C2 server delivers the BarbWire Backdoor. The downloader has a backup method of locating an alternative C2. If for any reason, the attackers wish to change the C2 from the one embedded, they can simply include the new destination in an SMS message. The downloader intercepts all incoming SMS messages. If one comes from the attackers, it can simply extract the new C2 details and download the backdoor.
The researchers describe BarbWire as, “a very capable piece of malware, and it is obvious that a lot of effort was put into hiding its capabilities behind string encryption, API hashing, and process protection. Its main goal is to fully compromise the victim machine, gaining access to their most sensitive data.”
BarbWire steals data via a range of file types, including PDFs, Office files, archives, image files, videos, and images. It also looks for external media such as a CD-ROM file – which suggests it may be looking for super-sensitive data that is often moved around physically rather than by telecommunication means. Stolen data is staged in a RAR archive and exfiltrated to the attackers’ C2 server. It also records audio and be used as a keylogger.